In my previous post I talked about something called String Hashing which is basically a function that generates a hash string based on a binary string.
In today post we will talk about on really useful algorithm called HMAC (Hash-based Message Authentication Code) which provides a way to generate a secure hash based on a string. Same as the hash function we wrote recently.
Why do we use something like HMAC?
On the internet we normally send messages between parties. The issue here is that, not being able to read the message doesn’t mean that you can’t interview with the meaning of the message. Anybody could interfiere with this communication and change the message between the parties.

This is when encrypted messages come into play and HMAC attempt protect this communication within the cipher and basically garantes that the messages hasn’t been changed.
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption.
One bit at the time
Let’s try to understand how a normal hashing function work.
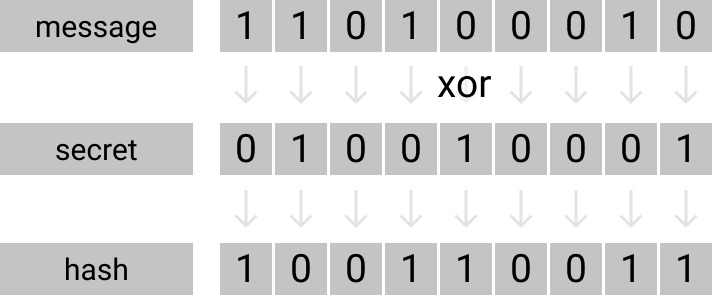
What we normally do is to XOR every bit of our message against out secret binary which will produce our final hash.
"my message" XOR "myrandomstring" = "myhash"The main issue is that a middle man could just reverse this process and see the actual message in the cipher.
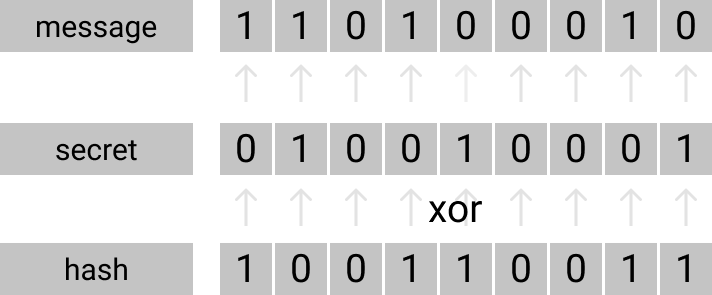
HMAC allows us to encrypt and sign the message with a Secret key and then only decrypt it using the same key. So, our middle man cannot see the message while is being sent.
This is an easy example of what would happen if a middle man tries to tweak our hash
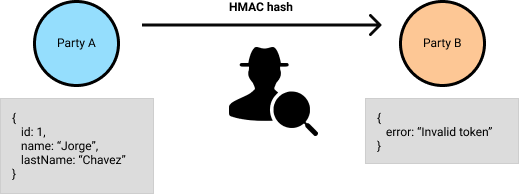
If the hash is valid, then the payload can be verified
